DEFCON:SM Car Hacking
Had some fun with the Car Hacking Village at this year's remote DEFCON Safe Mode. There seems to be a growing interest in automotive security which I've completely ignored until now, but decided to watch a beginner talk Cluster Fuzz by @mintynet about fuzzing the CAN bus.
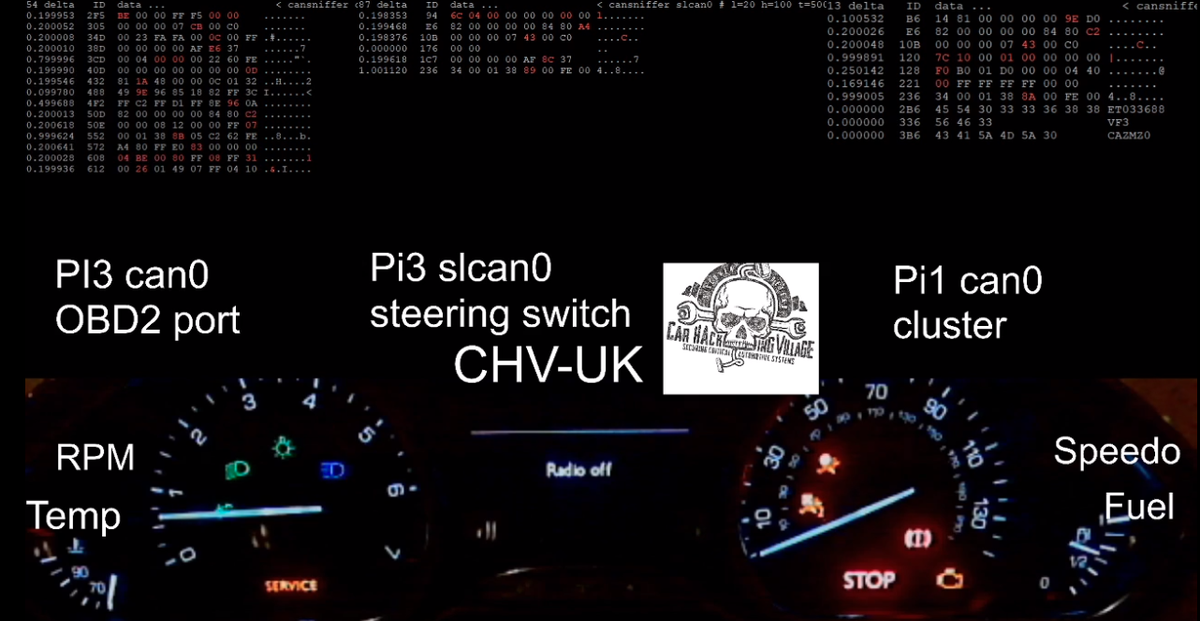
We had remote access to some cars (or parts of cars). Raspberry pis were connected to the CAN bus, allowing hackers to SSH in and send commands. The effect on the instrument panels could be seen via twitch.
I suppose this wasn't exploiting anything, but it was fun to discover how the systems interprets and responds to CAN messages from sensors and controls.
The tools used were:
- cansniffer to see the CAN bus traffic
- cansend to send a message
- cangen to fuzz
A CAN message consists of a 11-bit ID and up to 8 bytes of data.
The first step is to discover which IDs control what you're interested in. Then you can either make targetted changes or fuzz it.

As an example with a Peugeot 208 we found ID=F6 can reset power, control odometer reading, and control engine temperature meter. When I spammed the same message cangen can0 -g 0 -vvv -I f6 -L 8 -n 1000 -D 0800000032000000 the odometer displayed 80 km because 0x32 = 50 miles. If the 0x08 was set to 0x00 instead, the dashboard would reboot. The last 3 bytes were found to control the temperature meter. The IDs and data formats are different for different models of car.
After discovering the ID which controls lots of stuff I used cangen slcan0 -vvv -I $ID -g 5 -L8 which spammed random 8-byte messages to the bus. The result was chaos with the wash bottle squirting, relays going off and blinky lights. Anyway, was a bit of fun.
- Previous: Python tarfile infinite loop DoS
- Next: Google CTF 2020 Writeup